This week’s DevOps spotlight:
1. Jenkins on Kubernetes - Free Course Available Now!
We've launched a brand-new free course on deploying Jenkins on Kubernetes. We keep adding one lesson every day - Access it here
2. IPAM in Networking::
IP Address Management (IPAM) : This overview will help you understand how to manage IP addresses effectively within your network. Learn More
3. Wcurl Utility: A Handy Tool for Web Requests
Discover the utility of Wcurl, a versatile tool for making web requests. Perfect for DevOps engineers needing to interact with web services and APIs. Explore
🎁 Special Offers & Learning Resources
1. Save 25% on Kubernetes Certification Bundles:
Use code COMBUNDLE25 at CKA + CKS Bundle ($355 Savings) and KCNA + CKA ( $288 Savings)
2. Free Course on Gemini API by Google:
Expand your cloud knowledge with this free course on Google's Gemini API. A great resource for those interested in API management and cloud services. Access Here
3. Kubernetes Patterns - Free eBook:
Download the "Kubernetes Patterns" eBook for free and gain valuable insights into Kubernetes design patterns and best practices. Download Now
🔍 Research & Insights
1. Kube-Proxy 𝘀𝘁𝗮𝘁𝗶𝘀𝘁𝗶𝗰 𝗺𝗼𝗱𝗲 𝗿𝗮𝗻𝗱𝗼𝗺 𝗽𝗿𝗼𝗯𝗮𝗯𝗶𝗹𝗶𝘁𝘆.
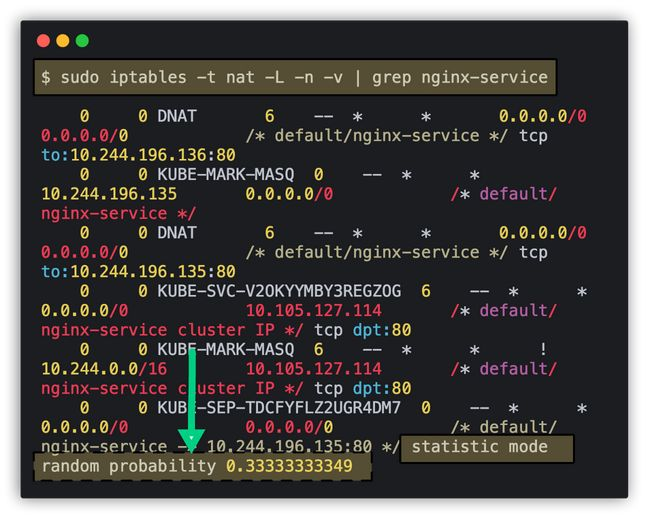
Ever wondered how Kubernetes services handle load balancing?
By default, the kube-proxy component in Kubernetes uses iptables for routing requests. (Supports IPVS as well)
I got curious about how it manages load balancing behind the scenes, and I discovered something interesting: a feature in iptables called 𝘀𝘁𝗮𝘁𝗶𝘀𝘁𝗶𝗰 𝗺𝗼𝗱𝗲 𝗿𝗮𝗻𝗱𝗼𝗺 𝗽𝗿𝗼𝗯𝗮𝗯𝗶𝗹𝗶𝘁𝘆.
This feature is part of iptables and is used for packet filtering and network address translation. It allows you to create rules that match a specific percentage of packets at random.
For example, I tested a service endpoint pointing to a three pod deployemnt. It showed statistic mode random probability as 0.33 , essentially balancing the load across the three pods.
It is more of a probabilistic traffic distribution and not actual load balancing.-
- It doesn't consider the actual load on the servers.
- It doesn't guarantee an even distribution of traffic over time.
- It doesn't maintain session persistence
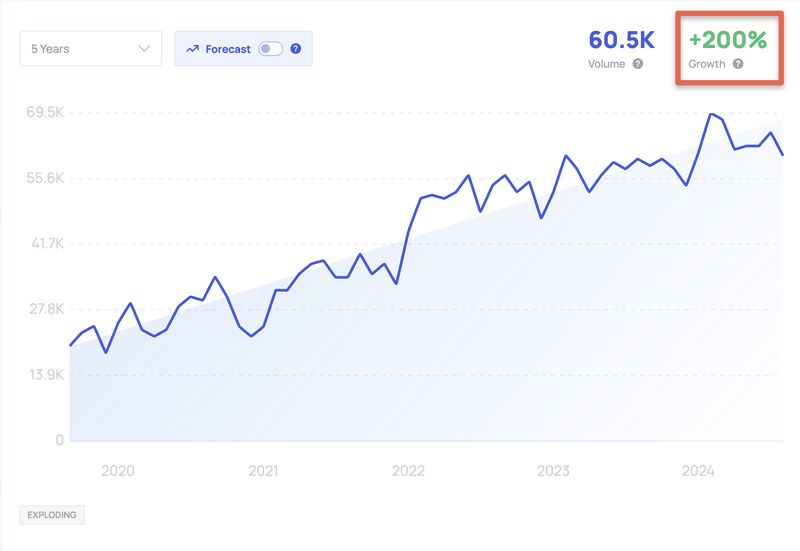
2. Searches for DevSecOps are skyrocketing—up 200% every year!
3. Istio utilizes 10 percent of hardware resources
Alibaba Cloud reported,A Kubernetes cluster comprising 500 nodes and 15,000 pods, and found it consumed 1,500 cores and 5,000 gigabytes of memory.
It also claimed that the sidecar's CPU and memory requirements grow even higher than that of the app.Google addressed some of these resource challenges with Ambient Mesh.
But as per Alibaba, Ambient Mesh improved performance but still required some proxies to reside within the user cluster.
Alibaba Cloud overcame these issues by building their own service mesh called Canal Mesh.It claims, Canal Mesh delivers throughput 𝟭𝟮.𝟯𝘅 𝗮𝗻𝗱 𝟮.𝟯𝘅 𝗵𝗶𝗴𝗵𝗲𝗿 than Istio and Ambient Mesh, respectively, while reducing CPU consumption compared to Istio.
This was achieved by moving proxies out of the user cluster, leaving only a minimal on-node proxy to manage security and observability. Additionally, it leverages eBPF-based kernel bypass and remote mTLS acceleration to optimize performance further.
1. 𝗥𝗲𝗺𝗼𝘁𝗲 𝗺𝗧𝗟𝗦 𝗮𝗰𝗰𝗲𝗹𝗲𝗿𝗮𝘁𝗶𝗼𝗻:It is a technique used to optimize the processing of mTLS connections by offloading the computationally intensive cryptographic operations to specialized hardware.A similar implementation can be done in k8s ingress controllers for TLS using device plugins & RuntimeClass.
𝟮. 𝗲𝗕𝗣𝗙-𝗯𝗮𝘀𝗲𝗱 𝗸𝗲𝗿𝗻𝗲𝗹 𝗯𝘆𝗽𝗮𝘀𝘀A technique used to enhance the performance of network operations by bypassing the traditional kernel network stack in LinuxRead about XDP (eXpress Data Path) to understand more on this.
𝗗𝗲𝘁𝗮𝗶𝗹𝗲𝗱 𝗖𝗮𝗻𝗮𝗹 𝗠𝗲𝘀𝗵 𝗣𝗮𝗽𝗲𝗿: https://dl.acm.org/doi/pdf/10.1145/3651890.3672221
Stay tuned for more updates and resources in next week's digest!
