What is Policy as Code: An Essential Guide for Beginners
Explore our in-depth guide on Policy as Code (PaC), a vital component of DevSecOps.

In this blog, we explore what Policy as Code is, how to enforce it, and the tools and workflows associated with it.
Policy as code is an important concepts every DevOps engineer should know.
If you're wondering what this means and why it matters, this guide is for you.
What is a Policy?
In literal terms, Policy = Rules.
In the context of IT Infrastructure, policies are rules or guidelines that dictate how infrastructure should be set up, managed, and maintained.
They ensure compliance with organizational standards, legal requirements, and internal security guidelines, maintaining consistency and security across environments.
Here are some practical examples of policies:
- Security Policy for Cloud Infrastructure: This could be a policy that dictates all cloud servers must have specific firewall settings or certain ports must be closed to enhance security. For instance, the policy might enforce that all web servers should only have ports 80 (HTTP) and 443 (HTTPS) open.
- Resource Allocation Policy: This policy would define the size and type of resources to be used in the cloud environment. For example, it might state that development environments should only use small to medium-sized virtual machines to control costs.
- Image Security Policy: It ensures that only approved, scanned and signed container images can be deployed on Kubernetes, reducing the risk of introducing vulnerabilities.
- Resource Quota Policy: This policy sets limits on the amount of resources (like CPU, memory, and storage) that a namespace or a project can use. It prevents any single project from consuming more than its fair share of resources, ensuring a balanced and efficient use of the cluster.
- Network Policy: This type of policy controls the flow of traffic between pods and services in the Kubernetes cluster. It can be used to restrict which pods can communicate with each other, enhancing the security and isolation of different services.
- Role-Based Access Control (RBAC) Policy: RBAC policies control who can access the Kubernetes API and what operations they can perform. For instance, a policy might allow only certain users or groups to create and manage deployments in a particular namespace.
So, who is responsible for creating these policies?
Usually these policies are documented and shared with project teams by the compliance or security teams.
Now that we have an understanding of what 'policy' means in DevOps/IaC, let's look at what 'policy as code' means.
What is Policy as Code (PaC)?
Simply put, Policy as Code is the idea of writing your organization's infrastructure rules and policies in a code format.
Unlike traditional methods that rely on manual processes and documentation, this approach uses code to automate and enforce policies across your IT infrastructure.
Creating policies as code often requires collaboration between different teams for effective policy implementation.
Why Policy as Code?
The manual management of policies often leads to inconsistencies and errors.
For example, when a new engineer joins the team, they must be made aware of existing policies. Without this knowledge, they may develop Infrastructure as Code (IaC) that does not comply with organizational standards.
Take, for instance, a policy that mandates specific tags for every virtual machine. If an engineer is unaware of this requirement, they might deploy virtual machines without the necessary tags, leading to non-compliance
Policy as Code addresses these challenges by offering:
- Consistency: Ensures policies are uniformly applied.
- Automation: Saves time and reduces human error.
- Scalability: Easily adapts as your organization grows.
- Security Testing: Ensures DevSecOps practices right from developers laptop.
How Does Policy as Code Work?
Policy as Code involves defining policies in a machine-readable format.
Tools like Checkov, Open Policy Agent or Kyverno help interpret and enforce these policies.
For instance, you can write a policy that checks if your cloud configurations meet security standards.
Or write a policy that doesn't allow the use of latest tag in contianer images.
So that question you might have is,
So how do we enforce this policies so that it can check all the IaC code developed by engineers?
The answer is Pull Request Workflow:
Then integrate your Policy as Code tool with the PR workflow. It follows shift-left approach, which means enforcing standards and policies early in the IaC development lifecycle.
The following image shows the workflow of policy as code.
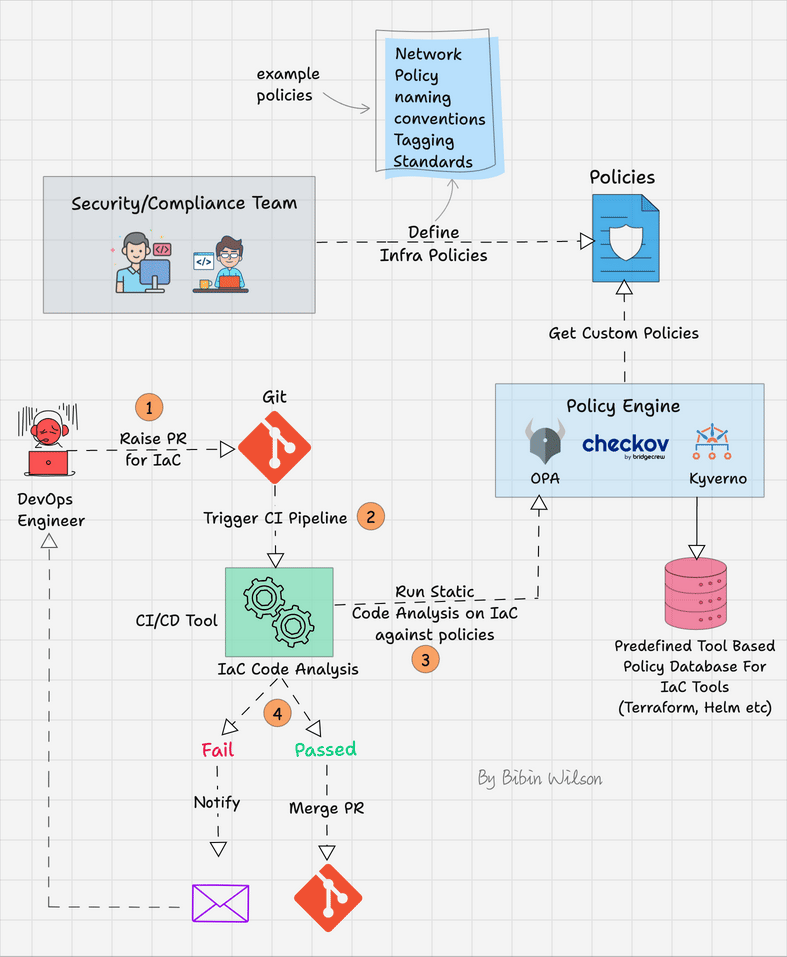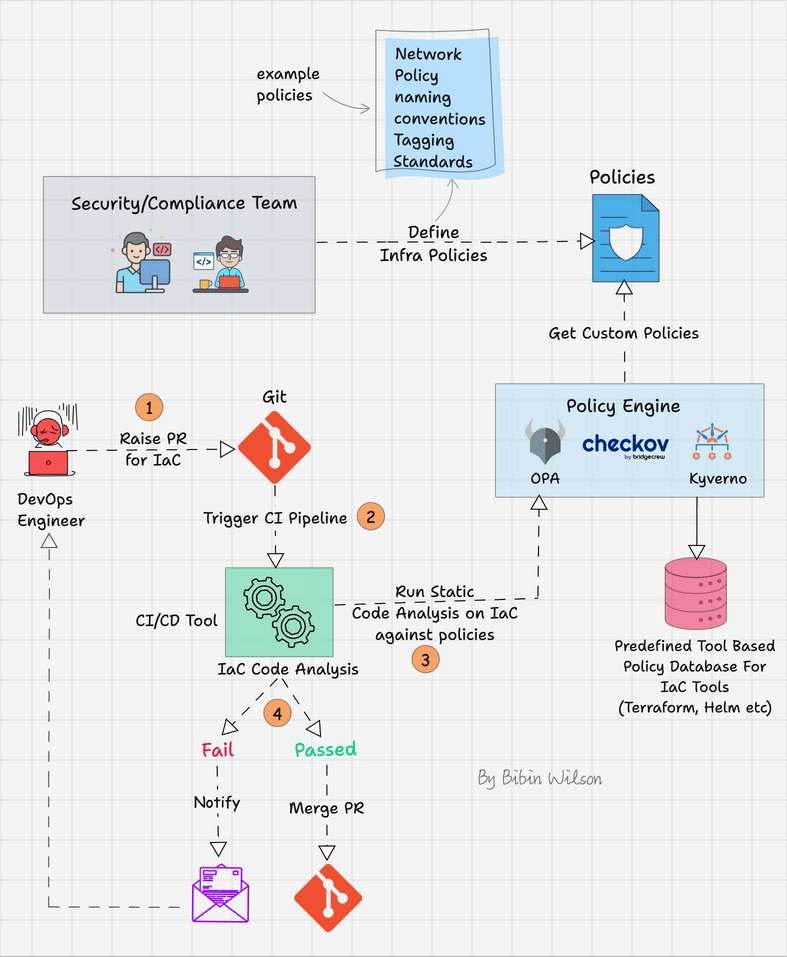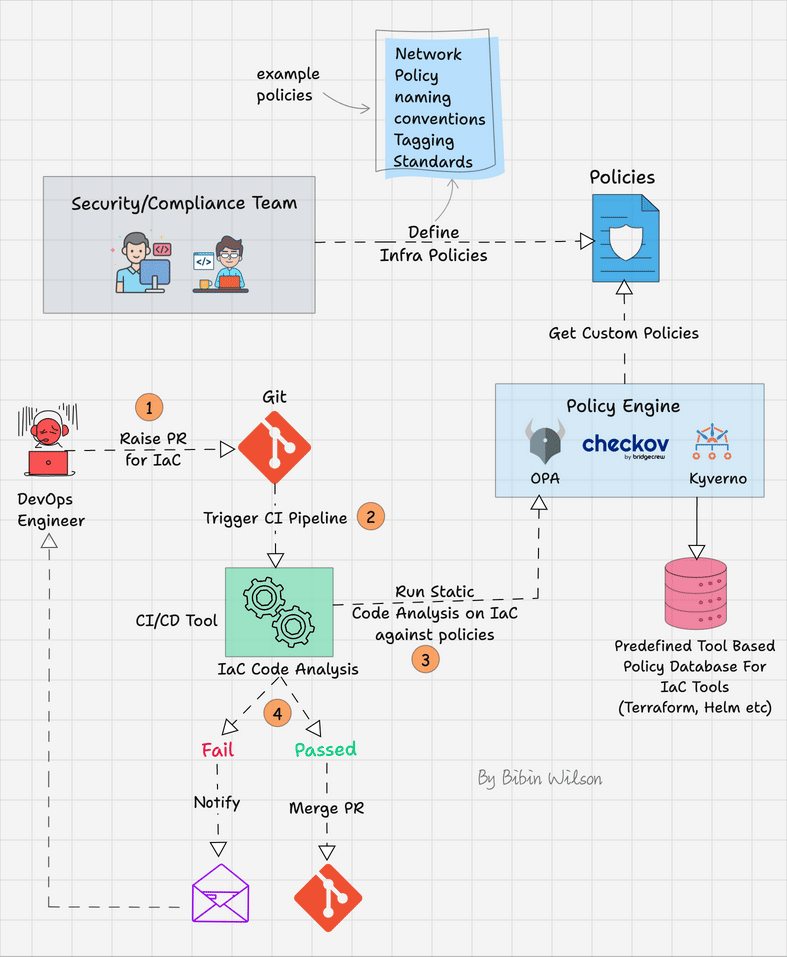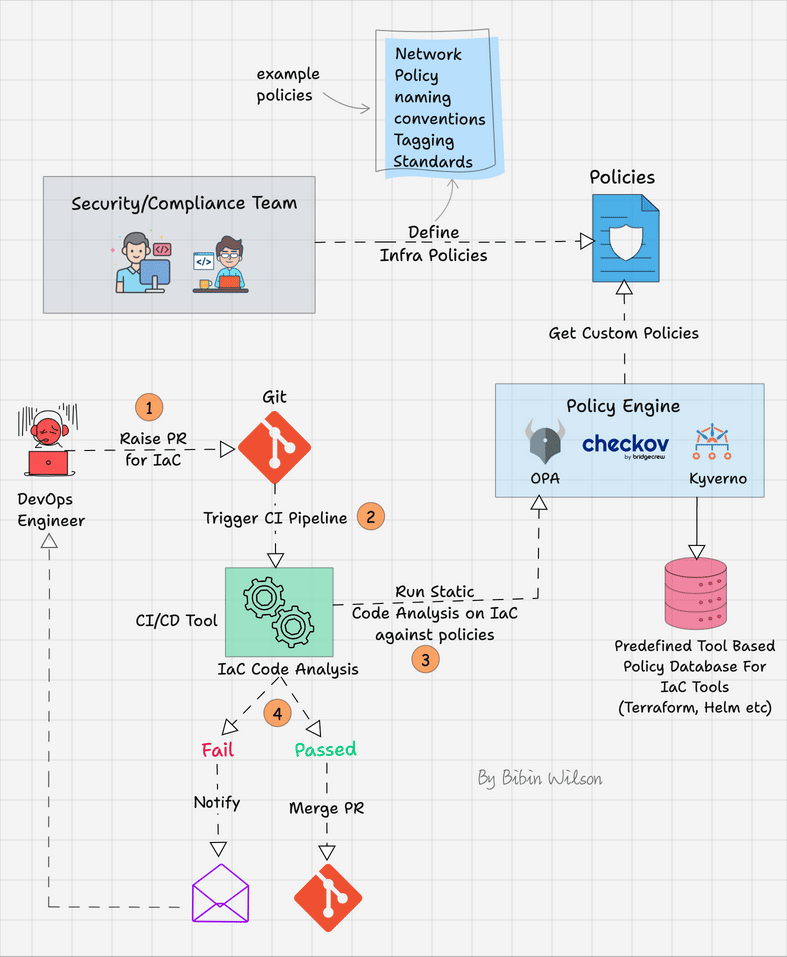
Here is how it works
- Start by defining clear and specific policies for your infrastructure. These policies might include security standards, resource allocation limits, naming conventions, etc. Use a Policy as Code tool like Checkov, Open Policy Agent (OPA), or Kyverno to define these policies.
- Establish a PR-based workflow for IaC development. Any changes to the infrastructure should be made via a branch, followed by a PR to merge the changes into the main branch.
- When a PR is created or updated, the policy as code tool automatically checks the proposed changes against the defined policies. This is typically done through a Continuous Integration (CI) pipeline using tools like Jenkins, GitHub Actions, GitLab CI/CD, etc.
- If the changes pass the policy checks, they move forward to the review stage where team members can review and discuss them. If the changes fail the checks, the engineer is notified to make the necessary adjustments.
- Once the PR is approved and it complies with all policies, it can be merged into the main branch. From there, the changes can be deployed to your infrastructure, often using Continuous Deployment (CD) tools.
However, ensuring that policies are applied before deploying to Kubernetes typically involves integrating policy checks into your Continuous Integration/Continuous Deployment (CI/CD) pipeline.
If the policy check fails, the pipeline should halt, and the team should be notified.
Documentation and Training
Ensure that all team members are trained on both the technical aspects of the tools and the importance of compliance with the policies.
Good documentation of the policies and processes is also important in implementing Policy as code.
Policy as Code Tools
Here's a list of open-source Policy as Code tools
1. Open Policy Agent (OPA):
OPA is a general-purpose policy engine that unifies policy enforcement across the stack. It's highly flexible and can be used for various types of policy decisions. OPA uses a high-level declarative language called Rego for policy definition.
It can be integrated with various systems like Kubernetes for admission control, Terraform for infrastructure, and even with CI/CD pipelines for validation of code and processes.
2. Kyverno
Kyverno is a policy engine designed for Kubernetes. It allows users to validate, mutate, and generate Kubernetes resource configurations using policies.
It's particularly useful for Kubernetes cluster management, ensuring that the Kubernetes configurations meet the required compliance and security standards.
3. Gatekeeper
Gatekeeper is an open-source policy engine that helps enforce policies and strengthen governance in a Kubernetes environment.
It's built around the Open Policy Agent (OPA) and allows users to validate and mutate Kubernetes resource configurations.
Gatekeeper is used for Kubernetes admission control, ensuring that cluster resource configurations are compliant with the defined policies.
3. Conftest
Conftest is a utility tool that helps users write tests against structured configuration data. It uses the Rego language from Open Policy Agent for writing policies.
It's often used for testing configuration files like JSON, YAML, HCL, or any other structured data to ensure compliance with policies.
4. Checkov
Checkov is an open-source Policy as code and static code analysis tool for infrastructure-as-code (IaC).
It scans cloud infrastructure managed in Terraform, Cloudformation, Kubernetes, ARM Templates, and Serverless framework to detect misconfigurations.
Checkov is known for its extensive library of pre-built policies that cover security and compliance best practices for AWS, Azure, and Google Cloud.
Checkov is often considered a part of the Policy as Code toolset, but it's more accurately described as a static code analysis tool that focuses on security and compliance in Infrastructure as Code (IaC).
It's commonly integrated into CI/CD pipelines to automatically scan for issues during the development process.
Conclusion
Policy as Code (PaC) plays a key role in DevSecOps practices by seamlessly integrating policy enforcement into the development, security, and operations pipeline.
Its importance can be summarized in several key aspects:
- Automated Compliance: Significantly reduces human errors and oversight.
- Security Integration: By embedding security policies directly into the development process, PaC aligns with the core principle of DevSecOps
- Efficiency and Speed: PaC streamlines the deployment process by providing immediate feedback on policy violations, enabling quick rectifications.
- Consistency and Standardization: PaC enforces consistent standards across all stages of development and operations.
- Continuous Improvement and Adaptability: As policies are codified, they can be versioned, tracked, and refined over time.
Bibin Wilson (authored over 300 tech tutorials) is a cloud and DevOps consultant with over 12+ years of IT experience. He has extensive hands-on experience with public cloud platforms and Kubernetes.