Managing sensitive data like API keys, passwords, and tokens securely in Kubernetes is critical for ensuring the security of applications. Kubernetes has several tools designed to manage secrets effectively.
In this guide, we will look into beginner-friendly explanations of some of Kubernetes's most popular secret management tools.
Best Secrets Management Tools
Here is the list of best secrets management tools for kubernetes that you should want to know.
1. External Secrets Operator (ESO)
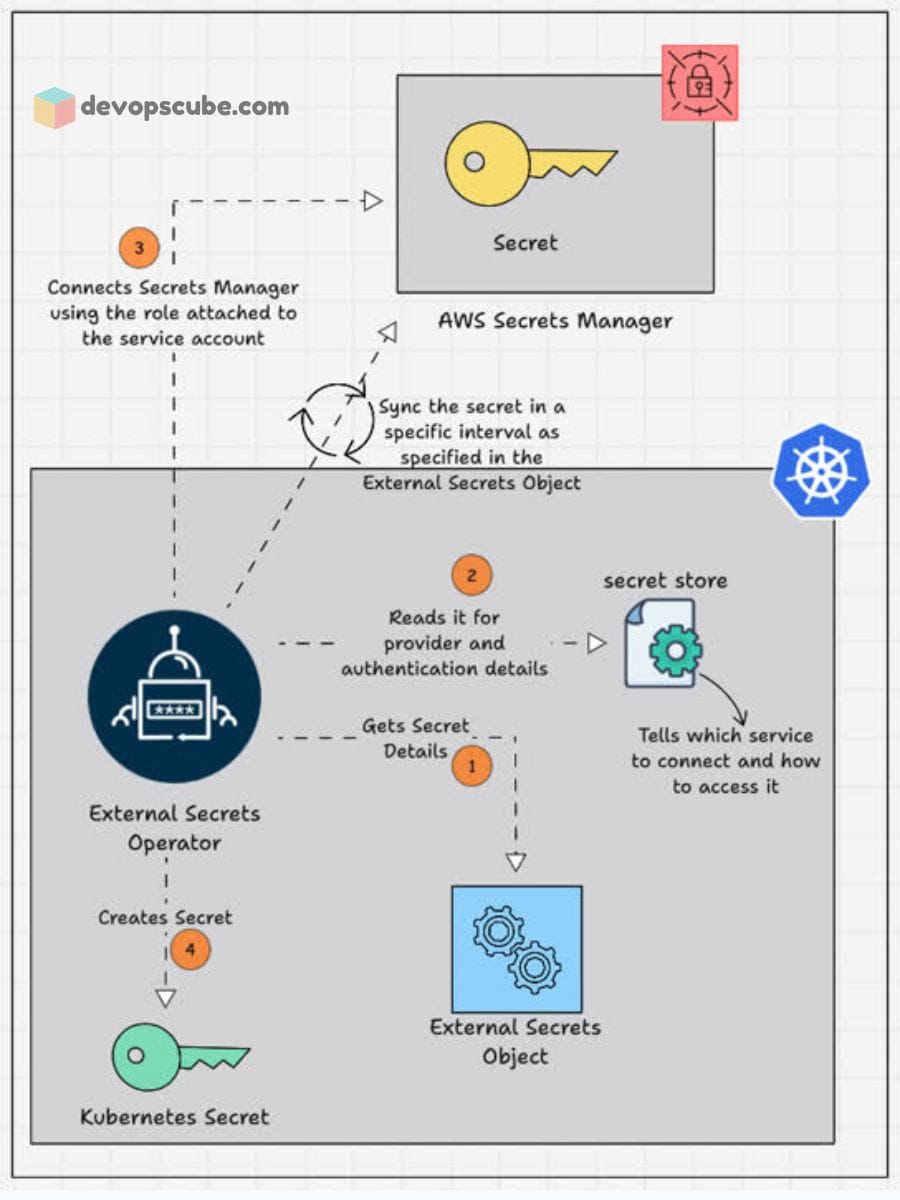
External Secrets Operator is an open-source Kubernetes operator that connects the gap between Kubernetes and external secret management systems.
It allows you to securely fetch secrets stored in external systems like AWS Secrets Manager, HashiCorp Vault, Google Secret Manager, and Azure Key Vault and insert them into your Kubernetes applications.
By using ESO, organizations can avoid storing sensitive data directly in Kubernetes etcd, reducing the risk of unauthorized access.
ESO is ideal for teams that already use external secret management tools and want to centralize secret storage outside of Kubernetes.
Key Features:
- Multi-backend support: Works with AWS Secrets Manager, Azure Key Vault, GCP Secret Manager, HashiCorp Vault, and more.
- Automatic synchronization: Automatically syncs secrets between external systems and Kubernetes.
- Custom resource definitions: Uses CRDs like
ExternalSecretto define secrets from external backends. - Encryption and decryption: Handles secure communication with external systems to fetch and manage secrets.
- RBAC: Supports detailed permissions within Kubernetes.
Pros:
- ESO makes integration with multiple external secret backends easier.
- It keeps secrets centralized outside Kubernetes, enhancing security.
- Automated synchronization ensures secrets are always up to date.
Cons:
- ESO requires configuration for each external secret provider.
- An additional component to manage within your Kubernetes cluster.
2. HashiCorp Vault Agent Injector

HashiCorp Vault Agent Injector is a specific tool that enables the effortless integration of HashiCorp Vault with Kubernetes.
It allows the automatic insertion of secrets into Kubernetes pods at runtime without storing them in the cluster.
This ensures secrets are always up-to-date and secure, utilizing Vault’s advanced capabilities, such as automatic secret generation and access control.
HashiCorp Vault Agent Injector is suited for organizations already using HashiCorp Vault for secrets management and requiring automatic secret injection in Kubernetes.
Key Features:
- Dynamic secret injection: Injects secrets into pods automatically at runtime based on labels.
- Short-lived secrets: Generates secrets with a limited lifespan, reducing security risks.
- Policy-driven access: Uses Vault policies to manage detailed access control for secrets.
- Multi-cloud support: Integrates with multiple cloud platforms for secret storage.
- High availability: Supports HA configurations for Vault.
Pros:
- Supports automatic, short-lived secrets for improved security.
- Integrates well with HashiCorp Vault’s policy-driven access control.
- No need to store secrets in Kubernetes etcd.
Cons:
- Requires HashiCorp Vault setup and management.
- Additional configuration overhead for Kubernetes deployments.
3. Sealed Secrets
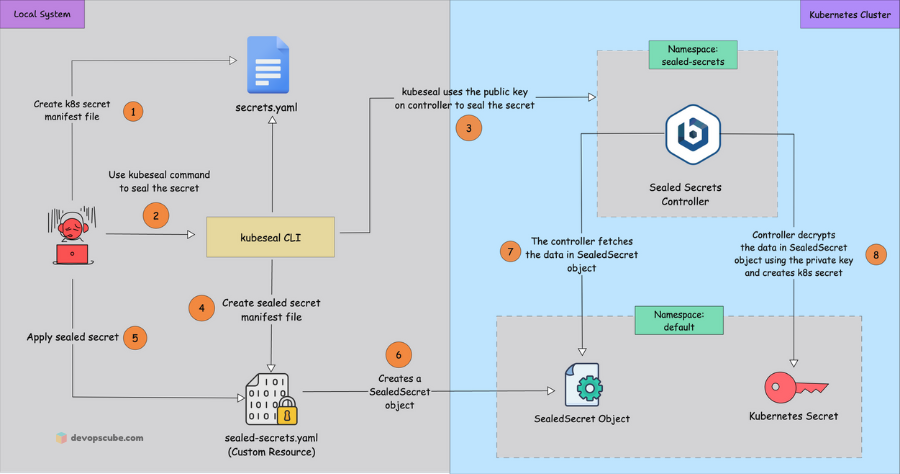
Sealed Secrets is an innovative tool developed by Bitnami to improve Kubernetes’s native secrets management capabilities. It allows users to encrypt secrets with a public key and store them securely in version control systems like Git.
So, only the Kubernetes cluster with the corresponding private key can decrypt and use these secrets, ensuring they remain secure.
Key Features:
- Public-key encryption: Encrypts secrets using a public key tied to a specific Kubernetes cluster.
- Version control integration: Stores encrypted secrets safely in Git repositories.
- CLI tools: Includes
kubesealfor encrypting secrets easily. - Namespace and name scoping: Limits decryption to specific namespaces and secret names.
- Cluster compatibility: Works with any CNCF-compliant Kubernetes cluster.
Pros:
- It will keep secrets safe in version control systems.
- Ensures the Sealed Secrets controller running in the Kubernetes cluster with the correct private key can decrypt secrets.
- Open-source and widely used in the community.
Cons:
- Requires the Sealed Secrets controller to be running in the cluster.
- It can be complex to manage at scale.
Sealed Secrets is perfect for teams that want to store secrets securely in Git repositories without compromising security.
4. Secrets Store CSI Driver
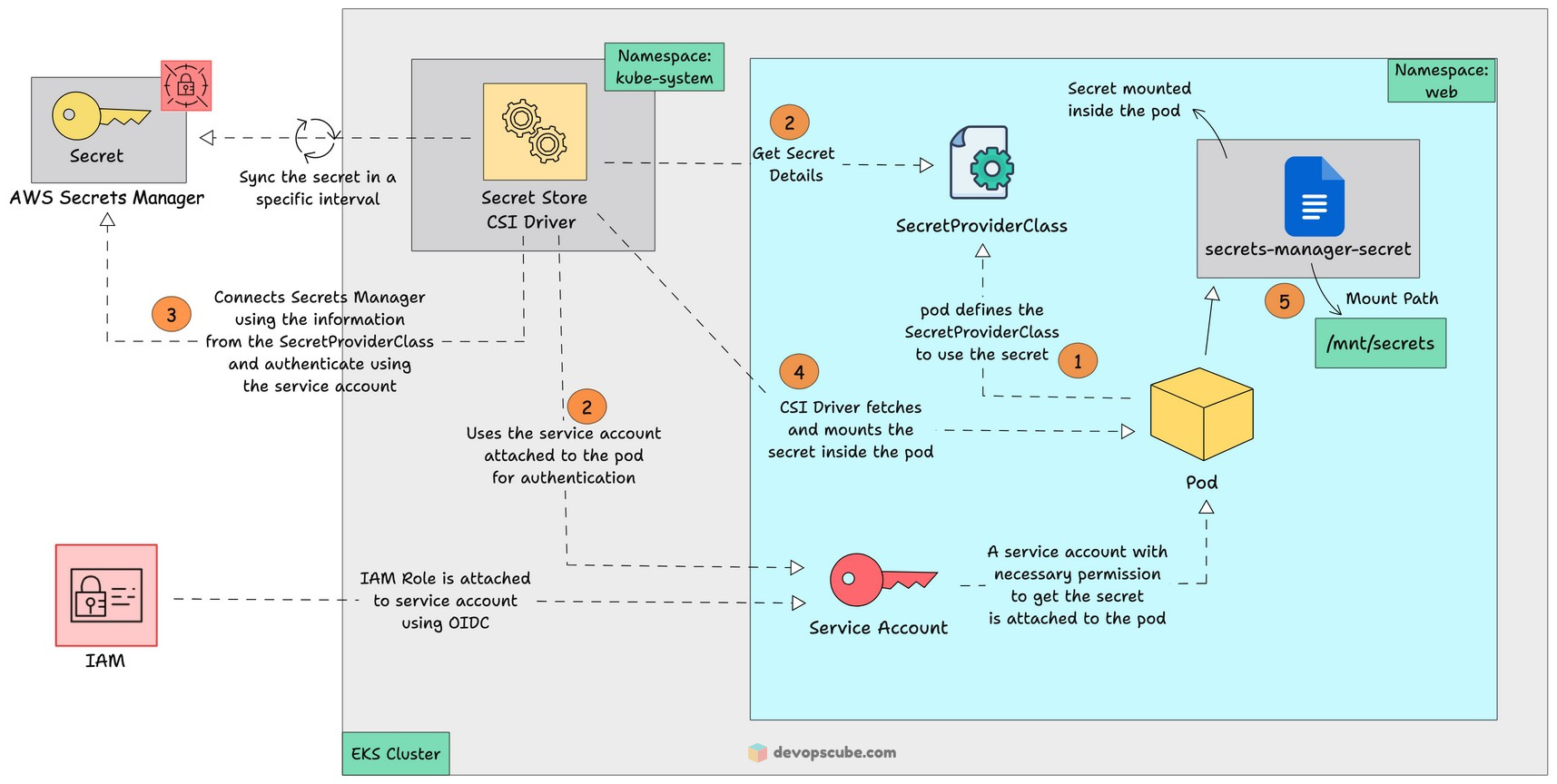
The Secret Store CSI Driver is a Kubernetes-native solution designed to integrate external secret management systems, such as AWS Secrets Manager, Azure Key Vault, and HashiCorp Vault, with Kubernetes.
It allows applications running in Kubernetes to securely access secrets without storing them in etcd, ensuring enhanced security and compliance for sensitive data.
Key Features:
- External secret provider integration: Supports AWS Secrets Manager, Azure Key Vault, HashiCorp Vault, and other external secret stores.
- IAM-based authentication: Uses IAM roles and other identity mechanisms for secure access control.
- Ephemeral secrets: Secrets are mounted as ephemeral volumes instead of being stored in Kubernetes Secrets.
- Automatic secret fetching: Retrieves secrets dynamically at runtime.
- Multi-cloud support: Works across multiple cloud providers.
Pros:
- Supports multiple cloud providers (AWS, Azure, GCP, Vault).
- Secrets are not stored in etcd, improving security.
- Uses IAM roles or cloud-native authentication for secure access.
- Secrets are updated automatically when modified in the external store.
Cons:
- Requires additional setup and configuration for providers.
- Secrets are not accessible via kubectl get secrets unless explicitly synced.
Secret Store CSI Driver is best for teams looking for a Kubernetes-native way to access secrets from external secret stores without persisting them in etcd. It is ideal for multi-cloud environments and security-focused workloads.
5. Mozilla SOPS (Secrets OPerationS)
Mozilla SOPS is a simple tool for encrypting sensitive data such as secrets and configuration files. It allows users to store encrypted secrets in version control systems like Git, ensuring data remains secure even if the repository is compromised.
SOPS integrates well with Kubernetes workflows by enabling teams to decrypt and utilize secrets dynamically during deployments.
Key Features:
- Encryption provider support: Works with AWS KMS, GCP KMS, Azure Key Vault, and PGP.
- File format support: Encrypts YAML, JSON, and other configuration files.
- GitOps compatibility: Enables teams to store and manage encrypted secrets in Git.
- Decryption on-demand: Secrets are decrypted only during deployment.
- Customizable encryption keys: Allows detailed control over encryption mechanisms.
Pros:
- Works efficiently with GitOps workflows.
- Easy to use.
- Maintains encrypted secrets in version control.
Cons:
- Requires additional tools or processes to decrypt secrets during deployment.
- Limited to encrypting static secrets.
Mozilla SOPS (Secrets OPerationS) is ideal for teams practicing GitOps and looking to store encrypted secrets in Git repositories.
6. Azure Key Vault Provider
The Azure Key Vault Provider is a Kubernetes-native integration for securely accessing secrets stored in Azure Key Vault.
It allows applications to fetch secrets and configurations directly from Azure Key Vault and insert them into pods as environment variables or files, getting rid of the need to store secrets in Kubernetes etcd.
Azure Key Vault Provider is best for teams running Kubernetes on Azure and depending on Azure Key Vault for secret management.
Key Features:
- Azure ecosystem integration: Works efficiently with Azure Key Vault and Active Directory.
- Environment variable injection: Inserts secrets into pods as environment variables or files.
- RBAC integration: Utilizes Azure RBAC for detailed access control.
- Automatic secret updates: Automatically updates secrets when they change in Azure Key Vault.
- Multi-tenant support: Allows use across multiple Azure subscriptions.
Pros:
- It has strong integration with Azure services.
- It can reduce dependency on Kubernetes’s etcd for secrets.
- It Supports strong authentication via Azure AD.
Cons:
- Limited to Azure infrastructure.
- It needs proper configuration and management of Azure AD.
7. Kamus
Kamus is an open-source encryption tool designed for Kubernetes. It encrypts secrets for specific applications, ensuring that only the designated application can decrypt and use them.
This approach minimizes the risk of unauthorized access to sensitive data and integrates well into existing CI/CD pipelines.
Kamus is perfect for developers who want application-specific encryption without exposing secrets to other services.
Key Features:
- Application-specific encryption: Encrypts secrets uniquely for each consuming application.
- Multi-cloud support: Works with AWS, GCP, and Azure.
- Flexible CLI and API: Provides a command-line interface and REST API for secret management.
- Custom encryption keys: Supports various key management systems for encryption.
- Kubernetes integration: Compatible with Kubernetes secrets.
Pros:
- It has application-specific encryption that improves security.
- It integrates efficiently with CI/CD pipelines.
- Open-source and customizable.
Cons:
- A learning process is needed for setup and usage.
- It has limited support compared to cloud-native tools
8. SecretHub
SecretHub is a fully managed, cloud-based secrets management platform that integrates with Kubernetes. It combines secret storage and distribution, offering developers a secure and convenient way to manage secrets across environments.
SecretHub provides detailed audit logs and access controls to ensure compliance and security.
Key Features:
- Centralized secret management: Stores and distributes secrets across all environments.
- Audit logging: Tracks all access and modifications to secrets.
- Access control: Supports role-based access control for users and applications.
- Kubernetes integration: Directly integrates with Kubernetes for secret input.
- Cross-environment compatibility: Works across development, staging, and production environments.
Pros:
- It is a fully managed service that reduces extra work.
- It will provide detailed audit trails and access control.
- It makes secret management across multiple environments easy.
Cons:
- It involves additional costs for the managed service.
- It depends on third-party infrastructure.
SecretHub is suitable for organizations looking for a cloud-native secrets management solution that integrates with Kubernetes and other tools.
9. Keywhiz
Keywhiz is an open-source tool designed for managing and distributing secrets securely. It is a focused secrets management system that ensures secrets are shared and stored securely across services and applications.
This tool is best for teams seeking a centralized, open-source solution for managing and auditing secrets.
Key Features:
- Secure API: Offers RESTful APIs for storing and retrieving secrets.
- Audit logging: Tracks secret access and modifications for compliance.
- Role-based access control: Ensures detailed permissions for secret access.
- Automatic secret expiry: Allows setting expiry dates for secrets to improve security.
- TLS encryption: Encrypts communication to ensure secure data transfer.
Pros:
- It has unified management of secrets across environments.
- It is an open source with active community support.
- It Provides strong auditing capabilities for compliance.
Cons:
- It needs additional setup and maintenance.
- It may not integrate as efficiently with Kubernetes as some cloud-native solutions.
Conclusion
Choosing the right secrets management tool for Kubernetes depends on your existing infrastructure, security requirements, and workflows.
Each tool has unique strengths, so check them based on your team’s needs.
Whether you prefer a cloud-native solution like AWS Secrets Manager or Azure Key Vault Provider, or an open-source option like Sealed Secrets or Kamus, Kubernetes provides the flexibility to secure your sensitive data effectively.