Understanding the OSI Model: Real World Examples
Understanding the OSI model is very important for DevOps engineers. IT Is one of the commonly asked DevOps interview question.
— Arun Lal
The OSI (Open Systems Interconnection) model is a theoretical framework to gain knowledge of the networking architecture and its functionality and this contains seven different stages.
Assume you are sending a letter to someone, maybe he is in another country, this letter goes through certain process and country-wise rules and regulations to reach them.
Now think of sending data across different part of the world.
The OSI model has a set of instructions, on how data is transmitted between networks. It is a seven-layer framework, and each layer is responsible for different kinds of operations.
The OSI Model
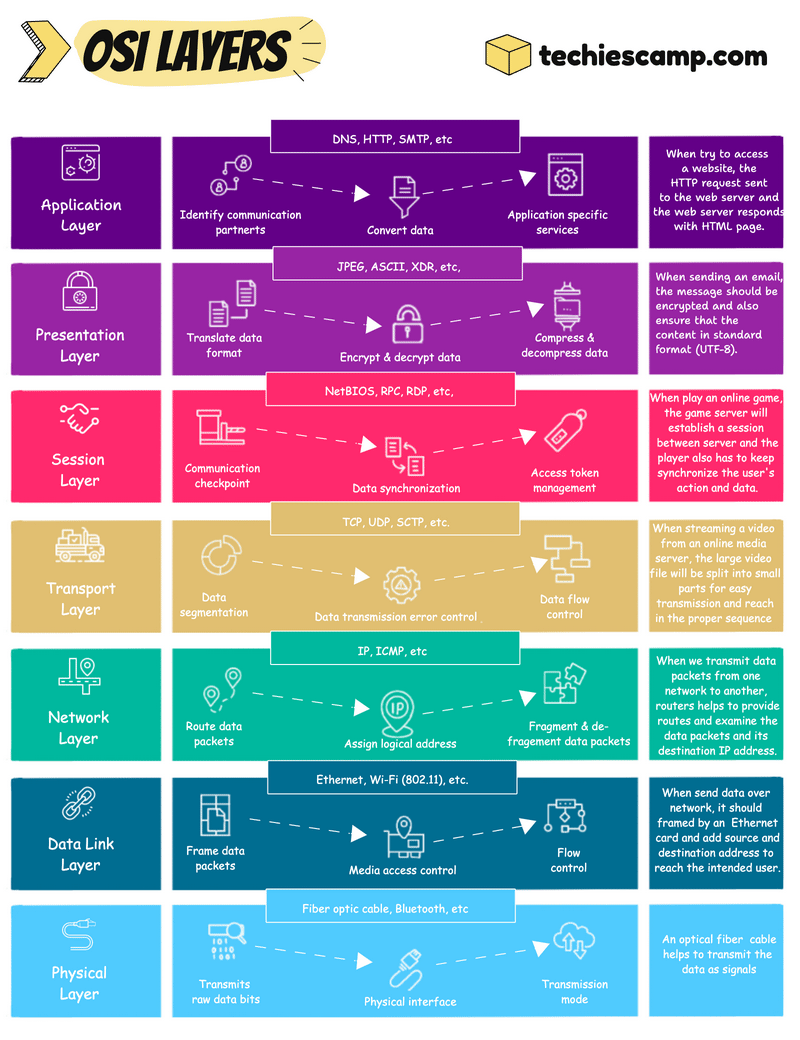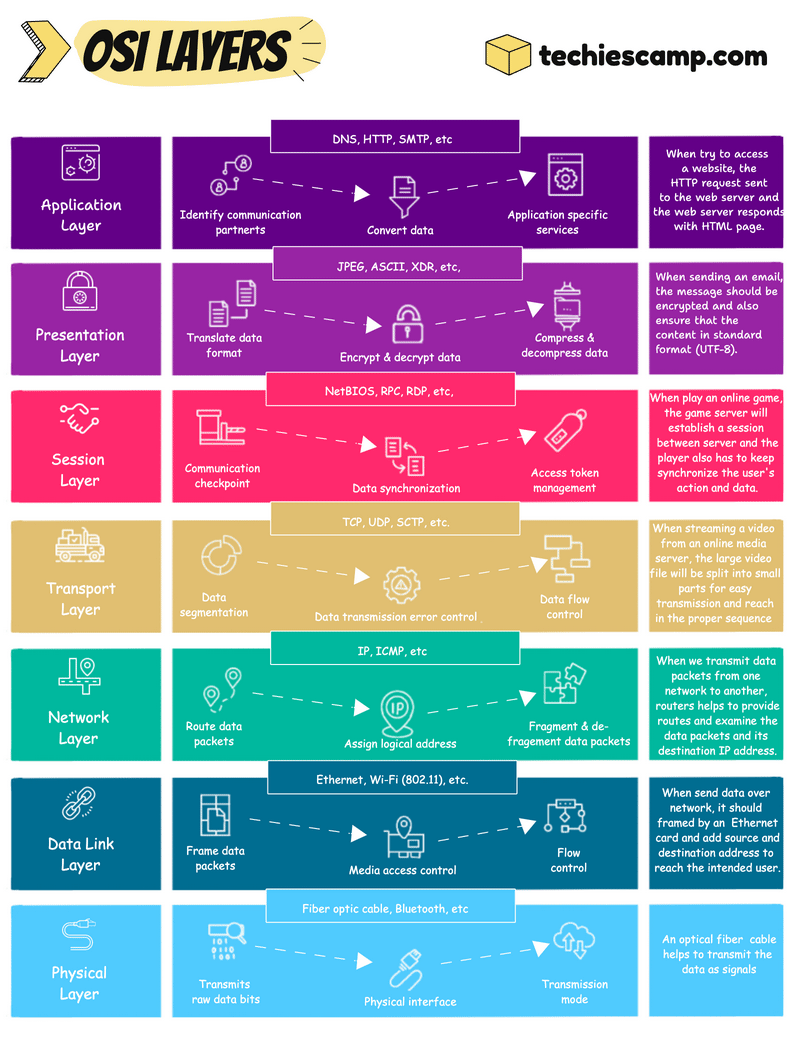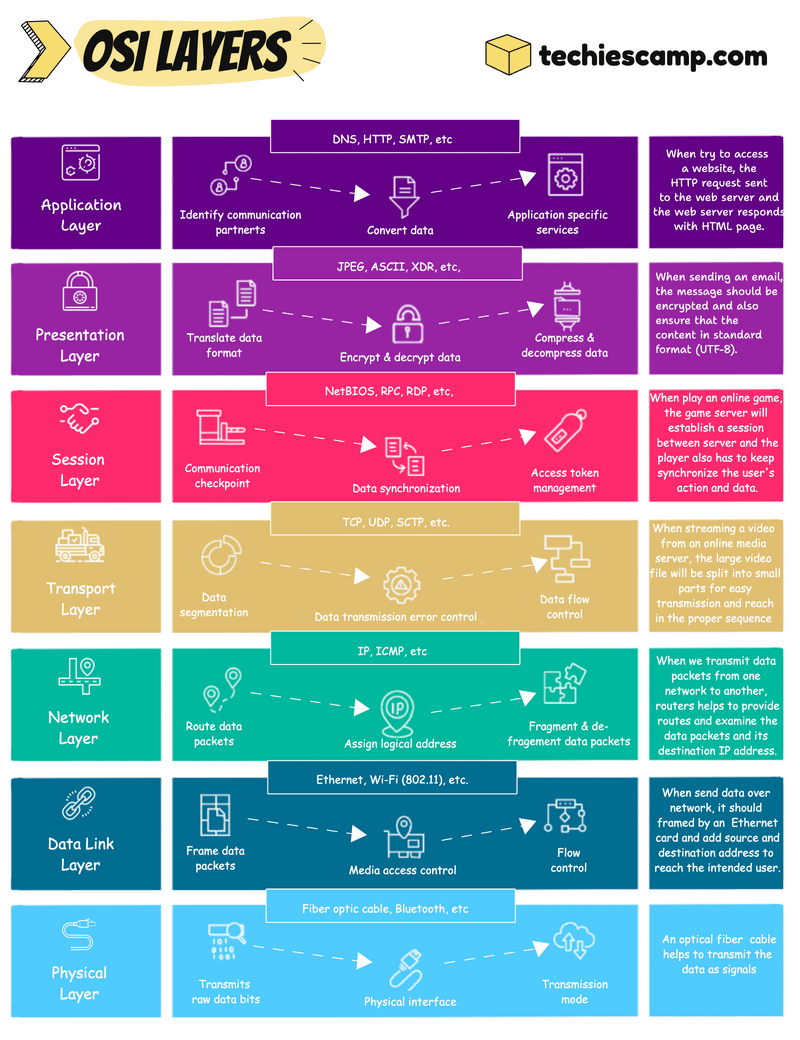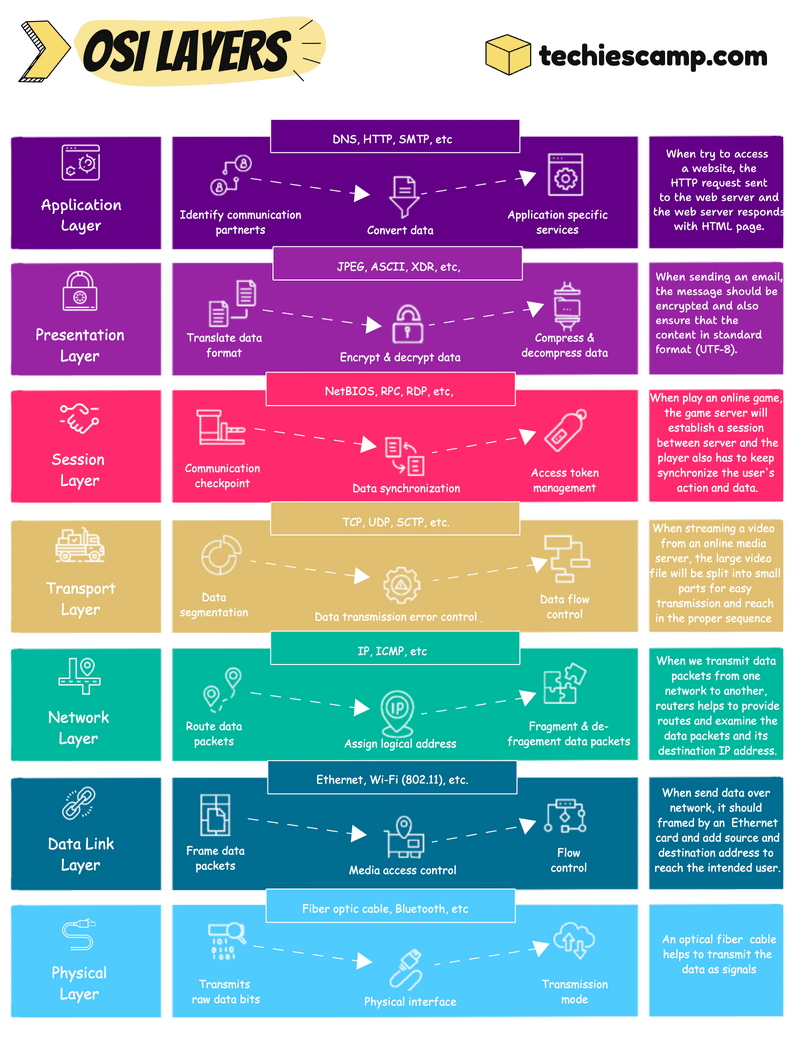
7. Application Layer
The application layer, we can say is closer to the users. This layer is not directly meant for the user’s face application but rather for which protocol or services help to get that interface to the user.
For example, if we are trying to access a website, the HTTP request will sent to the web server, then the verification process will happen between them, and then the web server shows the HTML web page to the user
6. Presentation Layer
The presentation layer will make the data presentable to the application and if the application doesn’t support the data format, then the presentation layer will do the translation.
This layer is also responsible for securing the data by doing encryption and decryption and helping to increase the speed of the transmission with its capability of compressing the data.
Let’s assume if a user sends a large important email to someone, the presentation layer will encrypt the data to prevent it from tampering and also compress it to make sure the mail will reach the receiver as fast as possible and translate the format, which is suitable to read the receiver.
5. Session Layer
The Session layer will establish multiple checkpoints between the communication.
The data will flow as multiple parts, all these parts should reach the receiver in a proper sequence. Session layer will do this job to synchronize these parts.
Playing online games is a perfect example of this layer. When you start playing an online game, a session will be created and synchronize the user data to the game server. This session persists until the game stops and also user data will be stored on the server during this time.
4. Transport Layer
The transport layer helps the data to reach the correct place and to achieve this, large data should be in small segments.
Also on the receiver side, this layer checks the error and ensures that the receiver is getting the proper data.
A user sends a larger file to a remote server via VPN, then the VPN uses the TCP or UDP protocol to ensure connection reliability and speed also it is a larger file, so it should be segmented as well as control the data flow for smooth transmission.
3. Network Layer
The network layer is very important if the communication occurs over the internet or different networks.
First, this layer will split the segments into smaller units called packets and will write the address to reach those packets in the intended destination.
This layer also chooses a short route to reach the destination.
We can take routers as an example to explain this layer. Routers make communication between different networks and also use a routing table to find the best route to transmit the data in a secure and reliable manner.
2. Data Link Layer
The data link layer is used to establish communication in a closed circle, like inside a network.
This further splits it as frames and makes a control to send those frames. It uses Media Access Control (MAC) addresses for communication.
Ethernet switch is a perfect example of this layer. Switches are used for inter-network communications and frame the data to travel to the physical objects.
1. Physical Layer
For communication, actual physical devices are also necessary and they can only transmit the data as signals through wired or wireless.
This layer converts the data as binaries and chooses a transmission mode that allows those bits to travel in cables and air.
Optical fiber cables and Bluetooth connectivity are a few examples of this layer.
The Importance of the OSI Model
- Currently, not every network communication follows the entire OSI model, though at least we can understand if any error happens in the current communication.
- This framework structure is universally the same, so we can understand an existing networking structure or it will help us when we build a new one.
- The OSI Model is like a blueprint for networking, each layer has different protocols and working nature, once we understand each layer, we can easily identify the vulnerabilities and develop security features for the specific layers.
Interview Preparation
Now let's look at some of the interview preparation scenarios related to the OSI model.
Question 1:
Your company has set up a Virtual Private Cloud (VPC) in AWS, the instances, which are created from this VPC couldn’t communicate with each other.
How would you troubleshoot, and what layer of the OSI model is relevant to rectify this issue?
Answer:
The network layer is responsible for the communication between instances in a VPC.
First need to check the route table to ensure the routes are properly configured to allow traffic between subnets.
Check the security group rules, that do not block the traffic to or from the instances.
Question 2:
You have hosted a web application in AWS, and because of the high traffic, now you have to find a way to optimize the traffic. which AWS service can help you solve this issue, and which OSI layer is responsible for this?
Answer:
Load Balancer is used to distribute the traffic between instances.
Different types of load balancers are available and also they work in different OSI layers.
For example, Network Load Balancer (NLB) works in (Layer 4), which is Transport Layer and Application Load Balancer (ALB) works in (Layer 7), which is Application Layer.
The Elastic Load Balancer (ELB) works with both Layer 7 and Layer 4, because, it uses the TCP, UDP, HTTP, and HTTPS protocols.
Question 3:
Can you give an example of an issue, which is related to the Transport Layer and how to resolve it?
The buffering issue is when you stream a video from an online media server.
The issue might be in the Transport Layer. This layer is responsible for managing the video segments properly and also ensuring the user is getting a smoother experience.
Question 4:
An organization is expanding its networks, while some users are facing issues accessing new applications. How to troubleshoot this with the help of the OSI model?
First, need to check the Physical Layer to ensure the physical components, such as cables and other devices, are connected properly.
Then need to check the Network Layer to verify the network routing and addressing to the new application are properly configured.
Moving to the Transport Layer to check the data transmission between the new application and the user.
Finally, analyze the Application Layer to ensure the application is properly configured.
Question 5:
Your company wants to implement a new protocol to encrypt the data transmission. In the OSI model, what are the layers you would consider for this implementation and why?
The Presentation Layer is where the data encryption happens, so this is important to secure our data.
The secure data packets reach the destination properly to establish the communication, for this, the Transport Layer is important.
Additionally, the Network Layer is necessary to show the correct and secure path to reach the destination.
Question 6:
Which OSI Layer does Kubernetes Service Operate?
Kubernetes services operate at Layer 4 (Transport Layer) of the OSI model. The Transport Layer is responsible for providing host-to-host communication services for applications.
Further Reference Topics
Software Defined Networking (SDN) is growing today, this helps to manage a larger network architecture and its components in a simple way using a centralized managing system.
Network Functions Virtualization (NFV) is an evolving technology, that helps to reduce the physical network components with virtual machines.
Quick UDP Internet Protocol (QUIC) is a Transport Layer protocol, that is built on top of User Datagram Protocol (UDP) to improve the data transfer speed.
Datagram Transport Layer Security (DTLS) is built for Datagram-based communication. this protocol is built on top of TLS to make the communication more secure.
These are some of the current growing technologies, evolving from the OSI model. This framework can’t be completely adopted for current networking architecture, even though, the concepts of the OSI model are useful to improve existing network architectures and to create new networking technologies.